- About Us
- Services
- Technology Leadership
- Technology Management
- Security Management
- Technology Innovation
-
Cyber Escape Rooms
A fun-filled and scientifically-designed solution to cyber training and team building
- Resources
- Podcasts
A fun-filled and scientifically-designed solution to cyber training and team building
In an increasingly complex environment, it extends beyond an organisation’s walls to the systems and networks of its ecosystem of third-party vendors.
When it comes to an organisation’s vendors, a breach in any link in the supply chain can have serious repercussions. Suppose your organisation’s data is vulnerable due to the practices of a third-party vendor, and that organisation failed to assess its security. In that case, the organisation may be liable if there is an incident.
Businesses must realise one simple fact – no matter their size, they supply goods and services and deal with their own suppliers. In short, every business has vendors and is a vendor, and because of that, establishing a vendor management program is a vital part of mitigating cyber risks to their organisation.
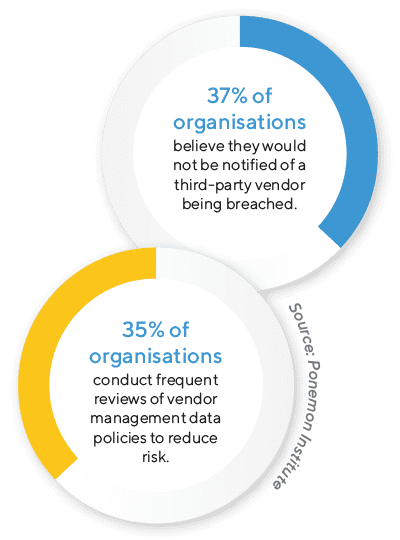
There are unavoidable risks associated with the loss of control that comes with outsourcing services and partnering with third-party businesses. The fundamental task of a vendor assurance program is to gauge and monitor the risk posed by third-party vendors and ensure those risks don’t reach unacceptable levels. Wyntec reviews and consistently monitors your vendor landscape and places risk scores on each vendor.
There are two major components to a vendor’s risk score:
Inherent risk is the risk the proposed vendor service(s) pose to your organisation if no security controls are in place. In determining inherent risk, organisations should consider questions such as operational dependency and what network assets and data the vendor can access.
Residual risk is the risk that the vendor poses after considering security controls to be applied. Each score takes into account the risk to business strategy, regulatory compliance, reputation, business operations, finance, information security and privacy and overall security.
Breaking the score into these categories allows your organisation to focus on specific areas of risk posed by specific vendor services so that the approach to each vendor isn’t too general. For example, a vendor with access to another organisation’s financial information may need additional security controls other vendors may not possess to maintain compliance with the Payment Card Industry Data Security Standard (PCI DSS).
Our vendor assurance program can help ensure that your network of vendors meet security requirements, reducing the risk of cyber attacks and data breaches.
Our team will work to ensure that your vendors comply with industry regulations and standards, reducing the risk of legal and financial compliance penalties.
By using our vendor assurance program, organisations can confidently work with only the most secure vendors ensuring you mitigate the risk of suffering the costly consequences of a breach or cyber attack from your vendor network.
Our program empowers organisations to gain a competitive advantage by enabling them to quickly access and utilise the best and most secure vendors for their business needs.
Wyntec can streamline and centralise the vendor information from all your vendors, making it easier for your organisation to manage and monitor vendors and any potential risks they pose.
Wyntec’s experienced team will monitor vendor performance, provide feedback, and hold vendors accountable for meeting your specific security expectations.
Building the right framework to implement vendor assurance programs is crucial. Our expert team will help you develop security standards and service-level agreements based on the risk and impact third parties have on your business. The risk scores we provide will assist in selecting the best vendors to serve your organisation’s needs and prioritise them from a security perspective
Questionnaires and requesting vendors to send documentation such as past audits that allow you to see what their security posture was in the past are best practice. To ensure the questionnaires can be relied upon, we utilise standards such as NIST and ISO 27001 as a base framework.
When a more thorough approach is required, our security architect can examine the vendor’s network configuration, encryption, and other security controls are working correctly. Penetration testing can be used to verify a vendor’s security defences and whether or not they remain in compliance. In addition, much can be gained by actually visiting a vendor’s site, which can give your organisation a sense not only of a vendor’s virtual security controls but their physical security defences as well.
To ensure the vendor maintain the necessary level of security, regular communication with your vendors is actioned, as well as periodic checkups for vendors whose importance to business operations and access to data and assets make them high risk.
Get in touch with the experts at Wyntec to explore how our Vendor Assurance Program can make a difference for your business
Level 11, 490 Upper Edward Street, Spring Hill QLD 4000
8:30AM to 5:00PM
1300 655 523